Contents

Sign in to your Android Police account
Summary
- A security researcher discovered a critical Google account bug that could have revealed users’ private recovery phone numbers, posing risks like SIM swap attacks and identity theft.
- The exploit involved a complex “attack chain” leveraging a JavaScript-disabled recovery form, publicly available display names (via Looker Studio), and phone number hints to brute-force full numbers in minutes.
- Google swiftly patched the vulnerability in May after being reported by the researcher in April, confirming the issue is now fixed.
Google account-related vulnerabilities aren’t all that uncommon. They’re patched swiftly before widespread exploitation, and most aren’t big enough to risk the average user or be headline-grabbing. That’s not necessarily the case with what a security researcher recently unearthed.
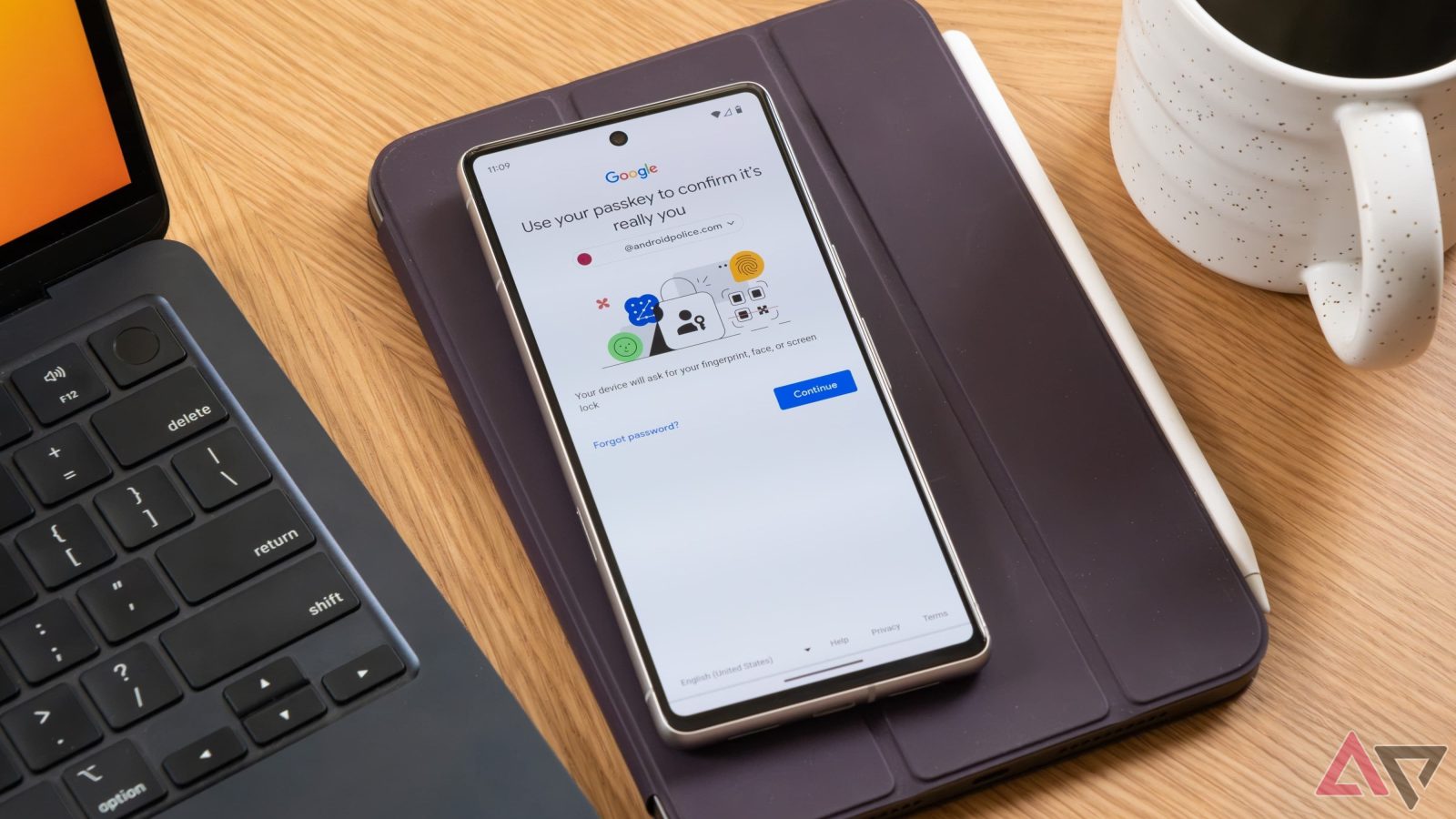
A bug tied to users’ Google accounts could, up until recently, be exploited to reveal the owner’s private recovery phone number without the user’s knowledge.

Related
The vulnerability was exposed by an independent researcher who goes by the name Brutecat (Skull on YouTube) (via TechCrunch) earlier today, but only after the vulnerability had been patched by Google.
The vulnerability, which, while it was active, could be used to reveal users’ phone numbers via Google’s account recovery feature. With other relevant information, which can be found online, threat actors leveraging this trick could perform SIM swap attacks and subsequently take over user accounts. Threat actors could also leverage the trick for identity theft or for targeted phishing and spam.
Rapid brute-force times
The exploit did not take advantage of a single flaw. Instead, it leveraged a sophisticated “attack chain” of several processes. According to Brutecat, it all began with the observation that the tech giant’s username recovery form still functioned without JavaScript. Such forms normally rely on complex JavaScript-based “BotGuard” solutions for anti-abuse measures, which is a notable observation considering most recovery forms have required javascript since 2018.
Brutecat then highlighted how Google’s username recovery form allows you to check whether a recovery email or phone number is associated with a specific display name. A subsequent request then allowed the researcher to verify a Google account’s existence with a given phone number and display name.
The researcher then found out that the Google account’s ‘forgot password’ flow offers a phone number hint — •• ••••••03, in the Netherlands, for example, as highlighted by the researcher. Now, if the exploiter knows the country the victim resides in, they can deduce the victim’s country code. This leaves just the remaining six digits to be brute-forced. For other countries, the number of unknown digits might vary.
The researcher also found a novel way to find out a Google account’s full display name. By creating a Looker Studio document and transferring its ownership to the victim’s Google account, the researcher could cause the victim’s full display name to appear on their Looker Studio homepage — under the document’s ‘owned by’ section.
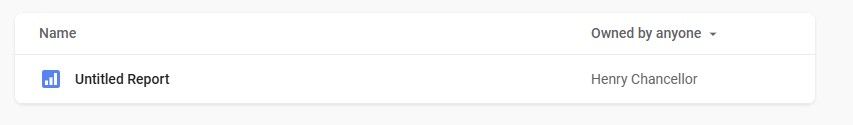
Source: Brutecat
Now, all that was left to do was to put all the steps and the information gathered through them together via an automated script. Using a server with consumer-grade specs, the researcher was able to run roughly 40,000 permutations per second. This allowed the script to brute-force its way through in minutes.
- United States (+1): Roughly 20 minutes required.
- United Kingdom (+44): Roughly 4 minutes required.
- Netherlands (+31): Roughly 15 seconds required.
- Singapore (+65): Roughly 5 seconds required.
According to the researcher, they reported the vulnerability to Google on April 14, and Google triaged it the very next day. In May, Google confirmed that it had rolled out mitigations, while the affected endpoint was globally deprecated.
“This issue has been fixed. We’ve always stressed the importance of working with the security research community through our vulnerability rewards program and we want to thank the researcher for flagging this issue,” said a Google spokesperson in a statement given to TechCrunch.
Related
What’s your reaction?
Love0
Sad0
Happy0
Sleepy0
Angry0
Dead0
Wink0








![so-long-and-farewell-from-the-android-police-podcast-[video]](https://betadroid.in/wp-content/uploads/2025/05/23445-so-long-and-farewell-from-the-android-police-podcast-video-370x250.jpg)

Leave a Reply
View Comments